diff options
| author | KN4CK3R <admin@oldschoolhack.me> | 2023-02-06 02:49:21 +0100 |
|---|---|---|
| committer | GitHub <noreply@github.com> | 2023-02-06 09:49:21 +0800 |
| commit | d987ac6bf1d78b3a9bbd213e73b871ebc687acb2 (patch) | |
| tree | c1f4840d675f6f99b38eb9684c7f6d2342f010d5 /modules/util/keypair.go | |
| parent | ff18d1744273d093d854f548662a0c204f220c16 (diff) | |
| download | gitea-d987ac6bf1d78b3a9bbd213e73b871ebc687acb2.tar.gz gitea-d987ac6bf1d78b3a9bbd213e73b871ebc687acb2.zip | |
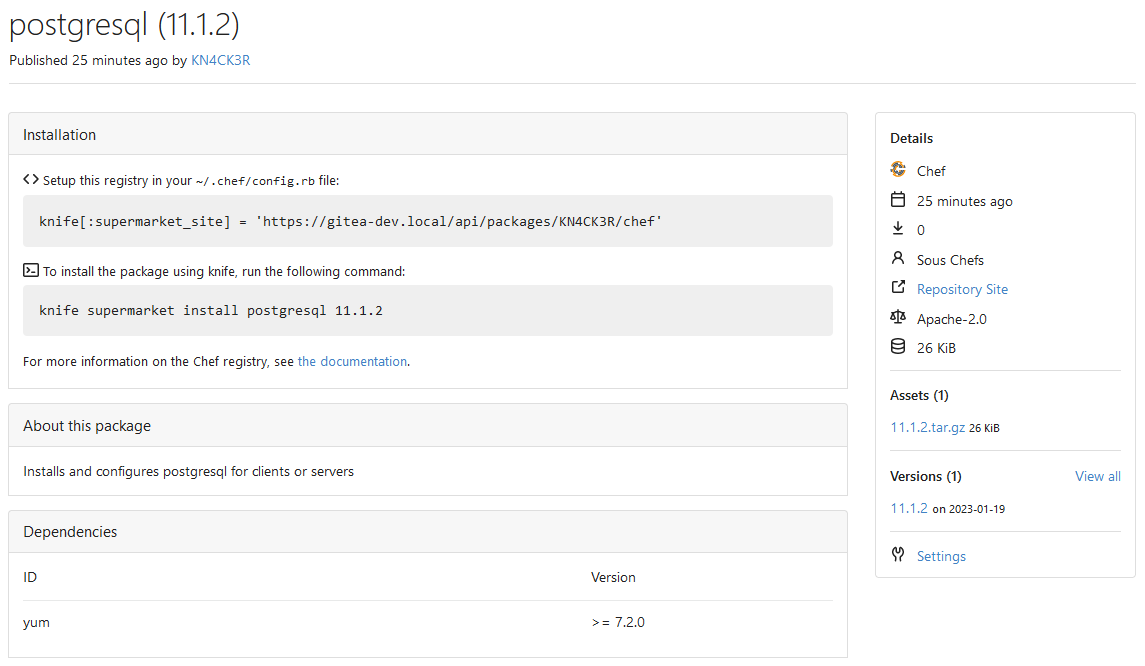
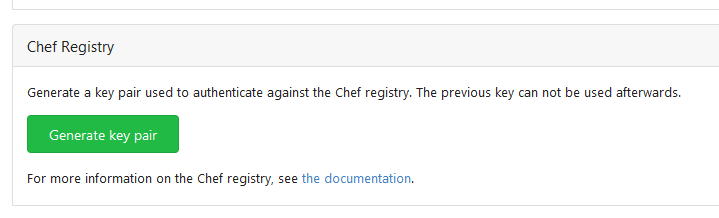
Add Chef package registry (#22554)
This PR implements a [Chef registry](https://chef.io/) to manage
cookbooks. This package type was a bit complicated because Chef uses RSA
signed requests as authentication with the registry.
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Diffstat (limited to 'modules/util/keypair.go')
| -rw-r--r-- | modules/util/keypair.go | 45 |
1 files changed, 45 insertions, 0 deletions
diff --git a/modules/util/keypair.go b/modules/util/keypair.go new file mode 100644 index 0000000000..5a3ce715a4 --- /dev/null +++ b/modules/util/keypair.go @@ -0,0 +1,45 @@ +// Copyright 2021 The Gitea Authors. All rights reserved. +// SPDX-License-Identifier: MIT + +package util + +import ( + "crypto/rand" + "crypto/rsa" + "crypto/x509" + "encoding/pem" +) + +// GenerateKeyPair generates a public and private keypair +func GenerateKeyPair(bits int) (string, string, error) { + priv, _ := rsa.GenerateKey(rand.Reader, bits) + privPem, err := pemBlockForPriv(priv) + if err != nil { + return "", "", err + } + pubPem, err := pemBlockForPub(&priv.PublicKey) + if err != nil { + return "", "", err + } + return privPem, pubPem, nil +} + +func pemBlockForPriv(priv *rsa.PrivateKey) (string, error) { + privBytes := pem.EncodeToMemory(&pem.Block{ + Type: "RSA PRIVATE KEY", + Bytes: x509.MarshalPKCS1PrivateKey(priv), + }) + return string(privBytes), nil +} + +func pemBlockForPub(pub *rsa.PublicKey) (string, error) { + pubASN1, err := x509.MarshalPKIXPublicKey(pub) + if err != nil { + return "", err + } + pubBytes := pem.EncodeToMemory(&pem.Block{ + Type: "PUBLIC KEY", + Bytes: pubASN1, + }) + return string(pubBytes), nil +} |
