diff options
| author | Jason Song <i@wolfogre.com> | 2022-12-20 17:07:13 +0800 |
|---|---|---|
| committer | GitHub <noreply@github.com> | 2022-12-20 17:07:13 +0800 |
| commit | 659055138b6d32492b20c9f4d1d5a3cdaa47188d (patch) | |
| tree | e2e7741be2b7b349e04f6901bff92b75b9b7c9ac /routers/web/repo/setting.go | |
| parent | 40ba750c4bf1f3f5f8dff5af57b2db4b600f237f (diff) | |
| download | gitea-659055138b6d32492b20c9f4d1d5a3cdaa47188d.tar.gz gitea-659055138b6d32492b20c9f4d1d5a3cdaa47188d.zip | |
Secrets storage with SecretKey encrypted (#22142)
Fork of #14483, but [gave up
MasterKey](https://github.com/go-gitea/gitea/pull/14483#issuecomment-1350728557),
and fixed some problems.
Close #12065.
Needed by #13539.
Featrues:
- Secrets for repo and org, not user yet.
- Use SecretKey to encrypte/encrypt secrets.
- Trim spaces of secret value.
- Add a new locale ini block, to make it easy to support secrets for
user.
Snapshots:
Repo level secrets:
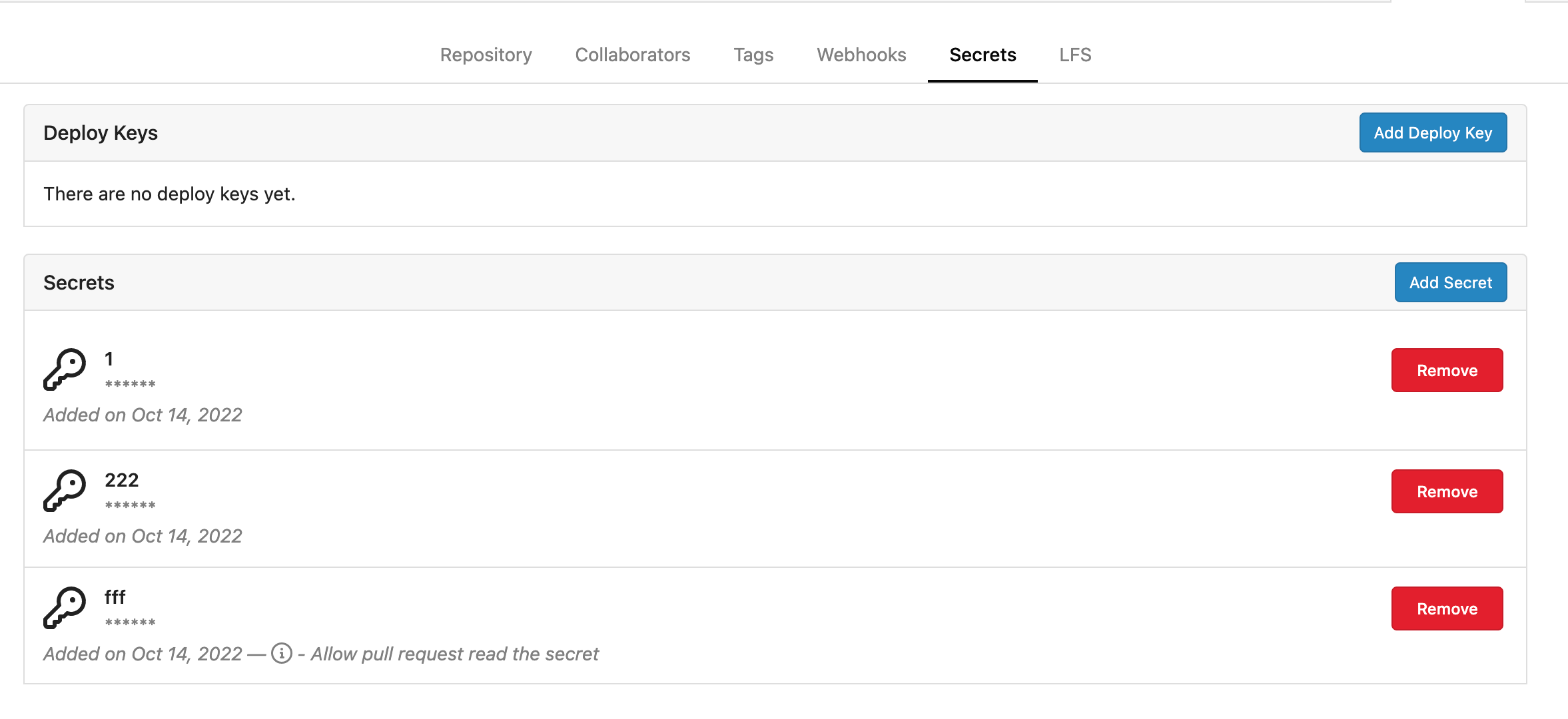
Rrg level secrets
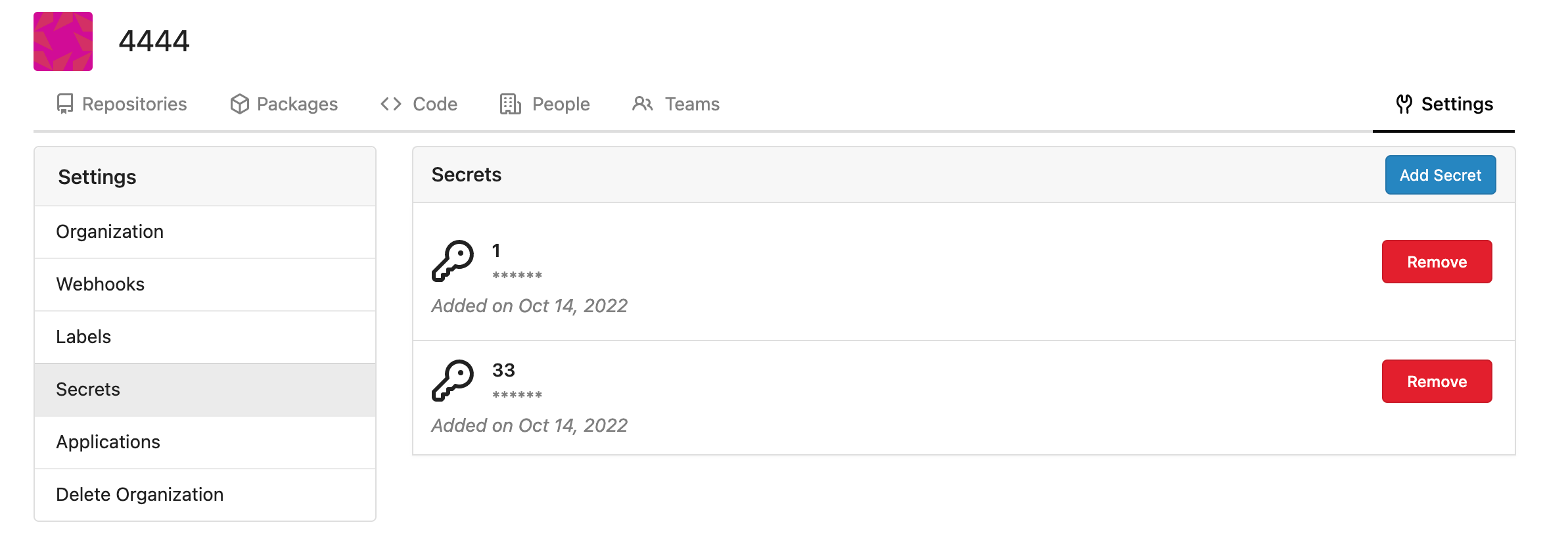
Co-authored-by: Lauris BH <lauris@nix.lv>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: KN4CK3R <admin@oldschoolhack.me>
Diffstat (limited to 'routers/web/repo/setting.go')
| -rw-r--r-- | routers/web/repo/setting.go | 40 |
1 files changed, 40 insertions, 0 deletions
diff --git a/routers/web/repo/setting.go b/routers/web/repo/setting.go index f35adcaa10..913ed6c7cb 100644 --- a/routers/web/repo/setting.go +++ b/routers/web/repo/setting.go @@ -19,6 +19,7 @@ import ( "code.gitea.io/gitea/models/organization" "code.gitea.io/gitea/models/perm" repo_model "code.gitea.io/gitea/models/repo" + secret_model "code.gitea.io/gitea/models/secret" unit_model "code.gitea.io/gitea/models/unit" user_model "code.gitea.io/gitea/models/user" "code.gitea.io/gitea/modules/base" @@ -1113,12 +1114,37 @@ func DeployKeys(ctx *context.Context) { } ctx.Data["Deploykeys"] = keys + secrets, err := secret_model.FindSecrets(ctx, secret_model.FindSecretsOptions{RepoID: ctx.Repo.Repository.ID}) + if err != nil { + ctx.ServerError("FindSecrets", err) + return + } + ctx.Data["Secrets"] = secrets + ctx.HTML(http.StatusOK, tplDeployKeys) } +// SecretsPost response for creating a new secret +func SecretsPost(ctx *context.Context) { + form := web.GetForm(ctx).(*forms.AddSecretForm) + + _, err := secret_model.InsertEncryptedSecret(ctx, 0, ctx.Repo.Repository.ID, form.Title, form.Content) + if err != nil { + ctx.Flash.Error(ctx.Tr("secrets.creation.failed")) + log.Error("validate secret: %v", err) + ctx.Redirect(ctx.Repo.RepoLink + "/settings/keys") + return + } + + log.Trace("Secret added: %d", ctx.Repo.Repository.ID) + ctx.Flash.Success(ctx.Tr("secrets.creation.success", form.Title)) + ctx.Redirect(ctx.Repo.RepoLink + "/settings/keys") +} + // DeployKeysPost response for adding a deploy key of a repository func DeployKeysPost(ctx *context.Context) { form := web.GetForm(ctx).(*forms.AddKeyForm) + ctx.Data["Title"] = ctx.Tr("repo.settings.deploy_keys") ctx.Data["PageIsSettingsKeys"] = true ctx.Data["DisableSSH"] = setting.SSH.Disabled @@ -1177,6 +1203,20 @@ func DeployKeysPost(ctx *context.Context) { ctx.Redirect(ctx.Repo.RepoLink + "/settings/keys") } +func DeleteSecret(ctx *context.Context) { + id := ctx.FormInt64("id") + if _, err := db.DeleteByBean(ctx, &secret_model.Secret{ID: id}); err != nil { + ctx.Flash.Error(ctx.Tr("secrets.deletion.failed")) + log.Error("delete secret %d: %v", id, err) + } else { + ctx.Flash.Success(ctx.Tr("secrets.deletion.success")) + } + + ctx.JSON(http.StatusOK, map[string]interface{}{ + "redirect": ctx.Repo.RepoLink + "/settings/keys", + }) +} + // DeleteDeployKey response for deleting a deploy key func DeleteDeployKey(ctx *context.Context) { if err := asymkey_service.DeleteDeployKey(ctx.Doer, ctx.FormInt64("id")); err != nil { |
