diff options
| author | Giteabot <teabot@gitea.io> | 2023-06-14 22:48:36 -0400 |
|---|---|---|
| committer | GitHub <noreply@github.com> | 2023-06-15 02:48:36 +0000 |
| commit | b45ea0280b6a48bbcd804a49ae3507d84f95b34f (patch) | |
| tree | 2d6c137c4c1deee38c13d4fdfa8074d011dab9fd /routers | |
| parent | 031ddfcb7b173684de66c622370ffeff5438ac52 (diff) | |
| download | gitea-b45ea0280b6a48bbcd804a49ae3507d84f95b34f.tar.gz gitea-b45ea0280b6a48bbcd804a49ae3507d84f95b34f.zip | |
Show OAuth2 errors to end users (#25261) (#25271)
Backport #25261 by @wxiaoguang
Partially fix #23936

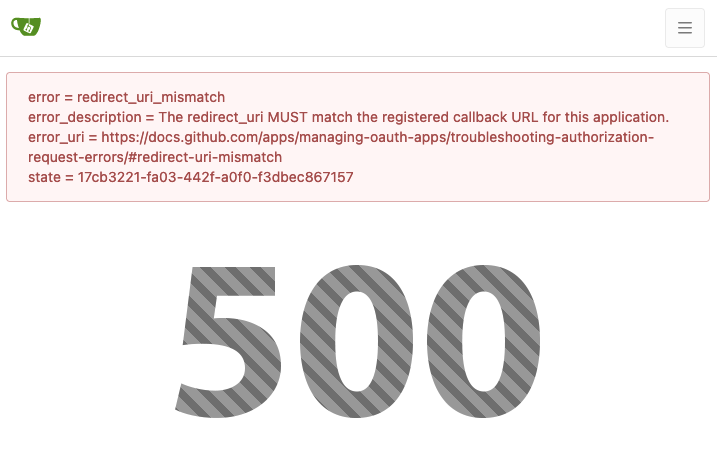

Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
Diffstat (limited to 'routers')
| -rw-r--r-- | routers/web/auth/oauth.go | 22 |
1 files changed, 19 insertions, 3 deletions
diff --git a/routers/web/auth/oauth.go b/routers/web/auth/oauth.go index 80f149d806..0ce3bbde00 100644 --- a/routers/web/auth/oauth.go +++ b/routers/web/auth/oauth.go @@ -4,7 +4,7 @@ package auth import ( - stdContext "context" + go_context "context" "encoding/base64" "errors" "fmt" @@ -12,6 +12,7 @@ import ( "io" "net/http" "net/url" + "sort" "strings" "code.gitea.io/gitea/models/auth" @@ -39,6 +40,7 @@ import ( "github.com/golang-jwt/jwt/v4" "github.com/markbates/goth" "github.com/markbates/goth/gothic" + go_oauth2 "golang.org/x/oauth2" ) const ( @@ -143,7 +145,7 @@ type AccessTokenResponse struct { IDToken string `json:"id_token,omitempty"` } -func newAccessTokenResponse(ctx stdContext.Context, grant *auth.OAuth2Grant, serverKey, clientKey oauth2.JWTSigningKey) (*AccessTokenResponse, *AccessTokenError) { +func newAccessTokenResponse(ctx go_context.Context, grant *auth.OAuth2Grant, serverKey, clientKey oauth2.JWTSigningKey) (*AccessTokenResponse, *AccessTokenError) { if setting.OAuth2.InvalidateRefreshTokens { if err := grant.IncreaseCounter(ctx); err != nil { return nil, &AccessTokenError{ @@ -886,6 +888,17 @@ func SignInOAuth(ctx *context.Context) { func SignInOAuthCallback(ctx *context.Context) { provider := ctx.Params(":provider") + if ctx.Req.FormValue("error") != "" { + var errorKeyValues []string + for k, vv := range ctx.Req.Form { + for _, v := range vv { + errorKeyValues = append(errorKeyValues, fmt.Sprintf("%s = %s", html.EscapeString(k), html.EscapeString(v))) + } + } + sort.Strings(errorKeyValues) + ctx.Flash.Error(strings.Join(errorKeyValues, "<br>"), true) + } + // first look if the provider is still active authSource, err := auth.GetActiveOAuth2SourceByName(provider) if err != nil { @@ -894,7 +907,7 @@ func SignInOAuthCallback(ctx *context.Context) { } if authSource == nil { - ctx.ServerError("SignIn", errors.New("No valid provider found, check configured callback url in provider")) + ctx.ServerError("SignIn", errors.New("no valid provider found, check configured callback url in provider")) return } @@ -920,6 +933,9 @@ func SignInOAuthCallback(ctx *context.Context) { ctx.Redirect(setting.AppSubURL + "/user/login") return } + if err, ok := err.(*go_oauth2.RetrieveError); ok { + ctx.Flash.Error("OAuth2 RetrieveError: "+err.Error(), true) + } ctx.ServerError("UserSignIn", err) return } |
