| Commit message (Collapse) | Author | Age | Files | Lines |
|---|
| |
|
|
|
|
|
|
|
|
|
|
|
| |
We wanted to be able to use the IAM role provided by the EC2 instance
metadata in order to access S3 via the Minio configuration. To do this,
a new credentials chain is added that will check the following locations
for credentials when an access key is not provided. In priority order,
they are:
1. MINIO_ prefixed environment variables
2. AWS_ prefixed environment variables
3. a minio credentials file
4. an aws credentials file
5. EC2 instance metadata
|
| |
|
|
| |
Syncs up docs associated to actions and deleted branch cleanup i.e. in
custom/app.example.ini and the config cheat sheet.
|
| |
|
|
|
| |
Add a configuration item to enable S3 virtual-hosted style (V2) to solve
the problem caused by some S3 service providers not supporting path
style (V1).
|
| |
|
|
|
|
| |
This is because it doesn't exist as an adapter. The `redis` adapter
already handles Redis cluster configurations.
Fixes #30534.
|
| |
|
|
|
|
|
|
|
|
|
|
|
| |
handling (#30622)
Follow #30454
And fix #24957
When using "preferred_username", if no such field,
`extractUserNameFromOAuth2` (old `getUserName`) shouldn't return an
error. All other USERNAME options do not return such error.
And fine tune some logic and error messages, make code more stable and
more friendly to end users.
|
| |
|
|
|
|
|
| |
Initial support for #25680
This PR only adds some simple styles from GitHub, it is big enough and
it focuses on adding the necessary framework-level supports. More styles
could be fine-tuned later.
|
| |
|
|
|
|
|
| |
Config section `[task]` has been deprecated in favor of `[queue.task]`
---------
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
|
|
| |
This PR adds the preferred_username claim as a possible username source
for the oauth2_client.
Closes #21518
|
| |
|
|
|
|
|
|
| |
This allows you to hide the "Powered by" text in footer via
`SHOW_FOOTER_POWERED_BY` flag in configuration.
---------
Co-authored-by: silverwind <me@silverwind.io>
|
| |
|
|
|
|
|
|
|
| |
## Changes
- Adds setting `EXTERNAL_USER_DISABLE_FEATURES` to disable any supported
user features when login type is not plain
- In general, this is necessary for SSO implementations to avoid
inconsistencies between the external account management and the linked
account
- Adds helper functions to encourage correct use
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
Previously, the default was a week.
As most instances don't set the setting, this leads to a bad user
experience by default.
## :warning: Breaking
If your instance requires a high level of security,
you may want to set `[security].LOGIN_REMEMBER_DAYS` so that logins are
not valid as long.
---------
Co-authored-by: Jason Song <i@wolfogre.com>
|
| |
|
|
|
| |
Extends #28075 to support [skip ci] inside PR titles.
Close #29265
|
| |
|
|
|
|
|
|
|
|
|
| |
app.ini (#29447)
Follow #29275
Extract from #20549
Fix #24716
---------
Co-authored-by: delvh <dev.lh@web.de>
|
| |
|
|
|
|
|
|
| |
app.ini (#29486)
Follow #29447
Fix #29454
Extract from #20549
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
In the refactoring of the configuration file #15807,
some lines were accidentally deleted:
DEFAULT_CLOSE_ISSUES_VIA_COMMITS_IN_ANY_BRANCH = false
ENABLE_PUSH_CREATE_USER = false
ENABLE_PUSH_CREATE_ORG = false
Fix #29510
---------
Co-authored-by: techknowlogick <matti@mdranta.net>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
|
|
|
|
|
|
|
|
|
| |
Extract from #20549
This PR added a new option on app.ini `[admin]USER_DISABLED_FEATURES` to
allow the site administrator to disable users visiting deletion user
interface or allow.
This options are also potentially allowed to define more features in
future PRs.
---------
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
- Databases are one of the most important parts of Forgejo, every
interaction uses the database in one way or another. Therefore, it is
important to maintain the database and recognize when the server is not
doing well with the database. There already is the option to log *every*
SQL query along with its execution time, but monitoring becomes
impractical for larger instances and takes up unnecessary storage in the
logs.
- Add a QoL enhancement that allows instance administrators to specify a
threshold value beyond which query execution time is logged as a warning
in the xorm logger. The default value is a conservative five seconds to
avoid this becoming a source of spam in the logs.
- The use case for this patch is that with an instance the size of
Codeberg, monitoring SQL logs is not very fruitful and most of them are
uninteresting. Recently, in the context of persistent deadlock issues
(https://codeberg.org/forgejo/forgejo/issues/220), I have noticed that
certain queries hold locks on tables like comment and issue for several
seconds. This patch helps to identify which queries these are and when
they happen.
- Added unit test.
(cherry picked from commit 9cf501f1af4cd870221cef6af489618785b71186)
---------
Co-authored-by: Gusted <postmaster@gusted.xyz>
Co-authored-by: Giteabot <teabot@gitea.io>
Co-authored-by: 6543 <6543@obermui.de>
|
| |
|
|
|
|
|
|
|
| |
With this option, it is possible to require a linear commit history with
the following benefits over the next best option `Rebase+fast-forward`:
The original commits continue existing, with the original signatures
continuing to stay valid instead of being rewritten, there is no merge
commit, and reverting commits becomes easier.
Closes #24906
|
| | |
|
| |
|
|
|
|
|
|
|
|
|
|
| |
Renames it to `ENABLED` to be consistent with other settings and
deprecates it.
I believe this change is necessary because other setting groups such as
`attachment`, `cors`, `mailer`, etc. have an `ENABLED` setting, but
`oauth2` is the only one with an `ENABLE` setting, which could cause
confusion for users.
This is no longer a breaking change because `ENABLE` has been set as
deprecated and as an alias to `ENABLED`.
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
Sometimes you need to work on a feature which depends on another (unmerged) feature.
In this case, you may create a PR based on that feature instead of the main branch.
Currently, such PRs will be closed without the possibility to reopen in case the parent feature is merged and its branch is deleted.
Automatic target branch change make life a lot easier in such cases.
Github and Bitbucket behave in such way.
Example:
$PR_1$: main <- feature1
$PR_2$: feature1 <- feature2
Currently, merging $PR_1$ and deleting its branch leads to $PR_2$ being closed without the possibility to reopen.
This is both annoying and loses the review history when you open a new PR.
With this change, $PR_2$ will change its target branch to main ($PR_2$: main <- feature2) after $PR_1$ has been merged and its branch has been deleted.
This behavior is enabled by default but can be disabled.
For security reasons, this target branch change will not be executed when merging PRs targeting another repo.
Fixes #27062
Fixes #18408
---------
Co-authored-by: Denys Konovalov <kontakt@denyskon.de>
Co-authored-by: delvh <dev.lh@web.de>
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
Mainly for MySQL/MSSQL.
It is important for Gitea to use case-sensitive database charset
collation. If the database is using a case-insensitive collation, Gitea
will show startup error/warning messages, and show the errors/warnings
on the admin panel's Self-Check page.
Make `gitea doctor convert` work for MySQL to convert the collations of
database & tables & columns.
* Fix #28131
## :warning: BREAKING :warning:
It is not quite breaking, but it's highly recommended to convert the
database&table&column to a consistent and case-sensitive collation.
|
| | |
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
- Resolves https://github.com/go-gitea/gitea/issues/22493
- Related to https://github.com/go-gitea/gitea/issues/4520
Some admins prefer all timestamps to display the full date instead of
relative time. They can do that now by setting
```ini
[ui]
PREFERRED_TIMESTAMP_TENSE = absolute
```
This setting is set to `mixed` by default, allowing dates to render as
"5 hours ago". Here are some screenshots of the UI with this setting set
to `absolute`:

---------
Signed-off-by: Yarden Shoham <git@yardenshoham.com>
Co-authored-by: delvh <dev.lh@web.de>
|
| |
|
| |
Follow #28626
|
| |
|
|
|
|
|
|
|
|
|
| |
The CORS code has been unmaintained for long time, and the behavior is
not correct.
This PR tries to improve it. The key point is written as comment in
code. And add more tests.
Fix #28515
Fix #27642
Fix #17098
|
| |
|
|
|
|
|
| |
default (#28548)
To keep user's privacy, make offline mode as true by default.
Users can still change it from installation ui and app.ini
|
| |
|
|
|
|
|
|
|
| |
Nowadays, cache will be used on almost everywhere of Gitea and it cannot
be disabled, otherwise some features will become unaviable.
Then I think we can just remove the option for cache enable. That means
cache cannot be disabled.
But of course, we can still use cache configuration to set how should
Gitea use the cache.
|
| |
|
|
|
|
|
|
| |
* Close #24483
* Close #28123
* Close #23682
* Close #23149
(maybe more)
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
## Changes
- Add deprecation warning to `Token` and `AccessToken` authentication
methods in swagger.
- Add deprecation warning header to API response. Example:
```
HTTP/1.1 200 OK
...
Warning: token and access_token API authentication is deprecated
...
```
- Add setting `DISABLE_QUERY_AUTH_TOKEN` to reject query string auth
tokens entirely. Default is `false`
## Next steps
- `DISABLE_QUERY_AUTH_TOKEN` should be true in a subsequent release and
the methods should be removed in swagger
- `DISABLE_QUERY_AUTH_TOKEN` should be removed and the implementation of
the auth methods in question should be removed
## Open questions
- Should there be further changes to the swagger documentation?
Deprecation is not yet supported for security definitions (coming in
[OpenAPI Spec version
3.2.0](https://github.com/OAI/OpenAPI-Specification/issues/2506))
- Should the API router logger sanitize urls that use `token` or
`access_token`? (This is obviously an insufficient solution on its own)
---------
Co-authored-by: delvh <dev.lh@web.de>
|
| |
|
|
|
|
|
|
|
|
|
|
| |
Adds the possibility to skip workflow execution if the commit message
contains a string like [skip ci] or similar.
The default strings are the same as on GitHub, users can also set custom
ones in app.ini
Reference:
https://docs.github.com/en/actions/managing-workflow-runs/skipping-workflow-runs
Close #28020
|
| |
|
|
| |
As title. Some attachments and file sizes can easily be larger than
these limits
|
| |
|
|
|
|
|
| |
as title
---
*Sponsored by Kithara Software GmbH*
|
| |
|
|
|
|
|
|
| |
https://github.com/go-gitea/gitea/blob/4a0103fa293cc42075d4a9c10ca4dffa9c2d3a40/modules/setting/ui.go#L24
https://github.com/go-gitea/gitea/blob/4a0103fa293cc42075d4a9c10ca4dffa9c2d3a40/modules/setting/ui.go#L77
---
*Sponsored by Kithara Software GmbH*
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
See [issue on
gitea.com](https://gitea.com/gitea/gitea-docusaurus/issues/38), copied
below for convenience:
> Hello, may I first confirm that the app.ini PROTOCOL config is case
sensitive (must be lowercase)?
>
> If so, I'd like to suggest for it to be highlighted in the [HTTPS
Setup](https://docs.gitea.com/administration/https-setup#using-the-built-in-server)
page.
> Perhaps something like:
> For the PROTOCOL=https field, make sure https is lowercase. Writing
PROTOCOL=HTTPS may result in a SSL_ERROR_RX_RECORD_TOO_LONG error on
Firefox or ERR_SSL_PROTOCOL_ERROR on Chrome and Edge.
>
> Background
> At first I carelessly wrote PROTOCOL=HTTPS in my app.ini, and Firefox
didn't allow me to connect because:
> Secure Connection Failed
> An error occurred during a connection to gitea.local.lan. SSL received
a record that exceeded the maximum permissible length.
> Error code: SSL_ERROR_RX_RECORD_TOO_LONG
> I spent maybe half an hour troubleshooting my certs, ports, and other
configs before backtracking to the start and realizing the
capitalization difference there 😅. When I changed that config to
lowercase, it worked.
For this PR I added the note in the Config Cheat Sheet page and fixed
the links to it from the HTTPS Setup page.
Was originally thinking to put the note in the HTTPS Setup page itself,
but since there are 2 sections referencing the PROTOCOL config, I was
thinking it'd be neater and more concise to put it in the Config Cheat
Sheet page instead. Especially since both sections already link to it,
and I actually tried to check that link quite early on in my
troubleshooting (but didn't pay much attention to it since the link was
broken).
## Before/After screenshots as per [this repo's
docs](https://github.com/go-gitea/gitea/tree/main/docs)
Before - links

Note: For this the links weren't broken, the links fix is because they
were broken on gitea.com's docs (see below).
After - links

Before - config cheat sheet
After - config cheat sheet

## Before/After screenshots as per [gitea.com's
docs](https://gitea.com/gitea/gitea-docusaurus)
Before - links
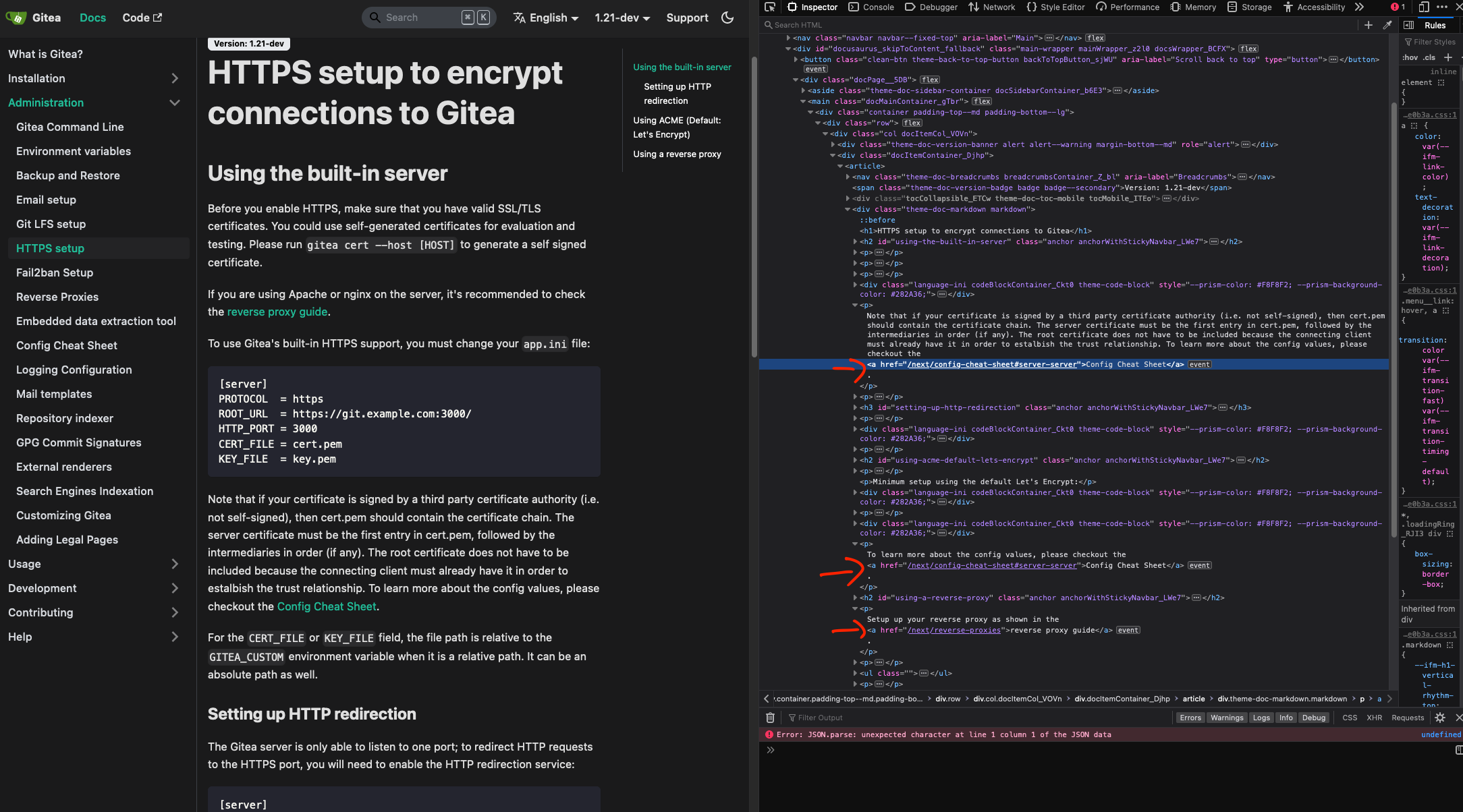
After - links
Before - config cheat sheet

After - config cheat sheet

|
| |
|
|
| |
configuraion enabled (#27482)
|
| | |
|
| |
|
|
|
|
| |
It remains to implement OAuth login in tea
https://gitea.com/gitea/tea/issues/598
Fixes #27510
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
Part of https://github.com/go-gitea/gitea/issues/27097:
- `gitea` theme is renamed to `gitea-light`
- `arc-green` theme is renamed to `gitea-dark`
- `auto` theme is renamed to `gitea-auto`
I put both themes in separate CSS files, removing all colors from the
base CSS. Existing users will be migrated to the new theme names. The
dark theme recolor will follow in a separate PR.
## :warning: BREAKING :warning:
1. If there are existing custom themes with the names `gitea-light` or
`gitea-dark`, rename them before this upgrade and update the `theme`
column in the `user` table for each affected user.
2. The theme in `<html>` has moved from `class="theme-name"` to
`data-theme="name"`, existing customizations that depend on should be
updated.
---------
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: Giteabot <teabot@gitea.io>
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
With this PR we added the possibility to configure the Actions timeouts
values for killing tasks/jobs.
Particularly this enhancement is closely related to the `act_runner`
configuration reported below:
```
# The timeout for a job to be finished.
# Please note that the Gitea instance also has a timeout (3h by default) for the job.
# So the job could be stopped by the Gitea instance if it's timeout is shorter than this.
timeout: 3h
```
---
Setting the corresponding key in the INI configuration file, it is
possible to let jobs run for more than 3 hours.
Signed-off-by: Francesco Antognazza <francesco.antognazza@gmail.com>
|
| |
|
|
| |
This PR makes the actions enabled by default, so people will find it
easier to enable actions in repository setting.
|
| |
|
|
|
|
|
|
|
|
|
| |
If the AppURL(ROOT_URL) is an HTTPS URL, then the COOKIE_SECURE's
default value should be true.
And, if a user visits an "http" site with "https" AppURL, they won't be
able to login, and they should have been warned. The only problem is
that the "language" can't be set either in such case, while I think it
is not a serious problem, and it could be fixed easily if needed.

|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
This feature was removed by #22219 to avoid possible CSRF attack.
This PR takes reverseproxy auth for API back but with default disabled.
To prevent possbile CSRF attack, the responsibility will be the
reverseproxy but not Gitea itself.
For those want to enable this `ENABLE_REVERSE_PROXY_AUTHENTICATION_API`,
they should know what they are doing.
---------
Co-authored-by: Giteabot <teabot@gitea.io>
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
| |
Currently, Artifact does not have an expiration and automatic cleanup
mechanism, and this feature needs to be added. It contains the following
key points:
- [x] add global artifact retention days option in config file. Default
value is 90 days.
- [x] add cron task to clean up expired artifacts. It should run once a
day.
- [x] support custom retention period from `retention-days: 5` in
`upload-artifact@v3`.
- [x] artifacts link in actions view should be non-clickable text when
expired.
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
This change was caused by #26271, for configuration as below:
```
[attachment]
ENABLE = true
PATH = data/attachments
MAX_SIZE = 100
MAX_FILES = 5
```
Before #26271, the resolved path is ${AppWorkPath}/${attachments.PATH}
(such as `/var/lib/gitea/data/attachments`)
After #26271, the resolved path is ${AppDataPath}/${attachments.PATH}
(such as `/var/lib/gitea/data/data/attachments`)
Fix https://github.com/go-gitea/gitea/issues/26864
Follow https://github.com/go-gitea/gitea/pull/26271
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
German Federal Office for Information Security requests in its technical
guideline BSI TR-02102-1 RSA Keylength not shorter than 3000bits
starting 2024, in the year 2023 3000bits as a recommendation. Gitea
should request longer RSA Keys by default in favor of security and drop
old clients which do not support longer keys.
https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Publikationen/TechnischeRichtlinien/TR02102/BSI-TR-02102.pdf?__blob=publicationFile&v=9
- Page 19, Table 1.2
---------
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| | |
|
| | |
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
This PR is an extended implementation of #25189 and builds upon the
proposal by @hickford in #25653, utilizing some ideas proposed
internally by @wxiaoguang.
Mainly, this PR consists of a mechanism to pre-register OAuth2
applications on startup, which can be enabled or disabled by modifying
the `[oauth2].DEFAULT_APPLICATIONS` parameter in app.ini. The OAuth2
applications registered this way are being marked as "locked" and
neither be deleted nor edited over UI to prevent confusing/unexpected
behavior. Instead, they're being removed if no longer enabled in config.

The implemented mechanism can also be used to pre-register other OAuth2
applications in the future, if wanted.
Co-authored-by: hickford <mirth.hickford@gmail.com>
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
---------
Co-authored-by: M Hickford <mirth.hickford@gmail.com>
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
|
|
|
|
|
|
|
| |
Not too important, but I think that it'd be a pretty neat touch.
Also fixes some layout bugs introduced by a previous PR.
---------
Co-authored-by: Gusted <postmaster@gusted.xyz>
Co-authored-by: Caesar Schinas <caesar@caesarschinas.com>
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
