| Commit message (Collapse) | Author | Age | Files | Lines |
|---|
| |
|
|
|
|
| |
Fixes https://github.com/go-gitea/gitea/issues/34591
A reference regarding the deletion of issue webhooks on GitHub:
https://docs.github.com/en/webhooks/webhook-events-and-payloads?actionType=deleted#issues
|
| |
|
| |
Remove unclear code
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
# Fix Feishu Webhook Signature Verification
This PR implements proper signature verification for Feishu (Lark)
webhooks according to the [official
documentation](https://open.feishu.cn/document/client-docs/bot-v3/add-custom-bot).
## Changes
- Implemented the `GenSign` function based on Feishu's official Go
sample code
- Modified the webhook request creation to include timestamp and
signature in the payload when a secret is configured
- Fixed the signature generation algorithm to properly use HMAC-SHA256
with the correct string format
## Implementation Details
The signature verification works as follows:
1. When a webhook secret is provided, a timestamp is generated
2. The signature string is created using `timestamp + "\n" + secret`
3. The HMAC-SHA256 algorithm is applied to an empty string using the
signature string as the key
4. The result is Base64 encoded to produce the final signature
5. Both timestamp and signature are added to the payload
According to Feishu's documentation, the timestamp must be within 1 hour
(3600 seconds) of the current time to be considered valid.
## Security Note
Feishu emphasizes the importance of keeping webhook URLs secure. Do not
disclose them on GitHub, blogs, or any public sites to prevent
unauthorized use.
## References
- [Feishu Custom Bot
Documentation](https://open.feishu.cn/document/client-docs/bot-v3/add-custom-bot)
---------
Co-authored-by: hiifong <i@hiif.ong>
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
Implements
- https://docs.github.com/en/rest/actions/workflow-jobs?apiVersion=2022-11-28#list-jobs-for-a-workflow-run--code-samples
- https://docs.github.com/en/rest/actions/workflow-jobs?apiVersion=2022-11-28#get-a-job-for-a-workflow-run--code-samples
- https://docs.github.com/en/rest/actions/workflow-runs?apiVersion=2022-11-28#list-workflow-runs-for-a-repository
- https://docs.github.com/en/rest/actions/workflow-runs?apiVersion=2022-11-28#get-a-workflow-run
- `/actions/runs` for global + user + org (Gitea only)
- `/actions/jobs` for global + user + org + repository (Gitea only)
- workflow_run webhook + action trigger
- limitations
- workflow id is assigned to a string, this may result into problems in
strongly typed clients
Fixes
- workflow_job webhook url to no longer contain the `runs/<run>` part to
align with api
- workflow instance does now use it's name inside the file instead of
filename if set
Refactoring
- Moved a lot of logic from workflows/workflow_job into a shared module
used by both webhook and api
TODO
- [x] Verify Keda Compatibility
- [x] Edit Webhook API bug is resolved
Closes https://github.com/go-gitea/gitea/issues/23670
Closes https://github.com/go-gitea/gitea/issues/23796
Closes https://github.com/go-gitea/gitea/issues/24898
Replaces https://github.com/go-gitea/gitea/pull/28047 and is much more
complete
---------
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
| |
1. use `test.MockVariableValue` as much as possible
2. avoid `time.Sleep` as much as possible
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
(#34481)
This PR changes 3rd party notifications wording on a PR review that
requests changes and can be considered a follow up for #5858 to also fix
#5857 in 3rd party notifications.
The difference in the actual notification would be the following:
```diff
- Pull request review rejected
+ Pull request review changes requested
```
While this is a simple string change at first look, it has a deeper UX
meaning.
# Motivation
We could observe that some developers are hesitant to press the "Request
changes" button since their peers first see that their changes were
rejected, thus a more appropriate wording that also falls in line with
the meaning and UI would be beneficial.
## Meaning
Pressing the `Request changes` button in a PR review means that as a
reviewer you are willing to merge the general change in a PR if changes
requested review comments are implemented.
Rejecting a PR on the other hand would be equivalent with closing it
since that change isn't welcome at all (e.g. out of scope feature).
## Sync with UI
The UI button says `request changes` and the other options

## Considered Problems
This might break some automation for users who rely on string matching.
|
| |
|
|
|
|
|
|
|
|
|
|
| |
Fixes [#34027](https://github.com/go-gitea/gitea/issues/34027)
Discord does not allow for description bigger than 2048 bytes. If the
description is bigger than that it will throw 400 and the event won't
appear in discord. To fix that, in the createPayload method we now slice
the description to ensure it doesn’t exceed the limit.
---------
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
|
|
|
|
| |
enable mirror, usestdlibbars and perfsprint
part of: https://github.com/go-gitea/gitea/issues/34083
---------
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
| |
enable testifylint rules disabled in:
https://github.com/go-gitea/gitea/pull/34054
|
| | |
|
| | |
|
| |
|
|
|
|
|
|
|
| |
Provide external Integration information about the Queue lossly based on
https://docs.github.com/en/webhooks/webhook-events-and-payloads?actionType=completed#workflow_job
Naming conflicts between GitHub & Gitea are here, Blocked => Waiting,
Waiting => Queued
Rationale Enhancement for ephemeral runners management #33570
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
Some visual improvement for the commit status webhook message introduced
by #33320
- use short commit SHA as already done in e. g. commit webhook
- fix spacing, link text
- do not set user link for internal gitea-actions user
Before:

After:
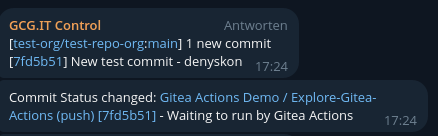
|
| |
|
|
|
|
|
|
|
|
|
|
| |
This is a X-GitHub Header port
* repository for repository webhooks (matches GitHub)
* organization for organization webhooks (matches GitHub)
* user for user webhooks (Gitea specific)
* system for system webhooks (Gitea specific)
* default for default hooks needs testing (Gitea specific)
- `X-Gitea-Hook-Installation-Target-Type`
- `X-GitHub-Hook-Installation-Target-Type`
|
| |
|
|
|
|
|
|
| |
Replace all contexts in tests with go1.24 t.Context()
---------
Co-authored-by: Giteabot <teabot@gitea.io>
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
|
|
|
|
|
|
| |
Gitea Actions generated target url doesn't contain host and port. So we
need to include them for external webhook visiting.
Fix #33603
---------
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
|
|
|
|
|
|
|
| |
Fix #32873
Fix #33201
~Fix #33244~
~Fix #33302~
depends on ~#33396~
A part of this PR should be backported to v1.23 manually.
|
| |
|
|
|
|
| |
This PR created a mock webhook server in the tests and added integration
tests for generic webhooks.
It also fixes bugs in package webhooks and pull request comment
webhooks.
|
| |
|
|
|
|
|
| |
Extract from #33320
This PR uses a map instead of a struct to store webhook event
information. It removes many duplicated functions and makes the logic
clearer.
|
| |
|
| |
And fix some FIXMEs
|
| |
|
| |
Close #27918
|
| |
|
| |
Fix #32897
|
| |
|
|
| |
Enables tenv and testifylint linters
closes: https://github.com/go-gitea/gitea/issues/32842
|
| |
|
|
|
|
|
|
|
|
|
|
| |
Resolves #32371.
#31970 should have just showed the commit summary, but
`strings.SplitN()` was misused such that we did not perform any
splitting at all and just used the message. This was not caught in the
unit test made in that PR since the test commit summary was > 50 (which
truncated away the commit description).
This snapshot resolves this and adds another unit test to ensure that we
only show the commit summary.
|
| |
|
|
|
|
|
|
|
|
|
| |
This PR introduces a new event which is similar as Github's. When a new
commit status submitted, the event will be trigged. That means, now we
can receive all feedback from CI/CD system in webhooks or other notify
systems.
ref:
https://docs.github.com/en/webhooks/webhook-events-and-payloads#status
Fix #20749
|
| |
|
|
|
|
|
|
|
|
|
| |
close #25833
Currently, the information for "requested_reviewers" is only included in
the webhook event for reviews. I would like to suggest adding this
information to the webhook event for "PullRequest comment" as well, as
they both pertain to the "PullRequest" event.
Also, The reviewer information for the Pull Request is not displayed
when it is approved or rejected.
|
| |
|
| |
Resolves #31668.
|
| | |
|
| |
|
|
|
|
| |
A more complete fix for #31588
1. Make "generic" code more readable
2. Clarify HTML or Markdown for the payload content
|
| |
|
|
|
|
|
|
|
|
|
|
| |
Enable [unparam](https://github.com/mvdan/unparam) linter.
Often I could not tell the intention why param is unused, so I put
`//nolint` for those cases like webhook request creation functions never
using `ctx`.
---------
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
|
| |
|
|
|
|
|
|
|
|
|
| |
Noteable additions:
- `redefines-builtin-id` forbid variable names that shadow go builtins
- `empty-lines` remove unnecessary empty lines that `gofumpt` does not
remove for some reason
- `superfluous-else` eliminate more superfluous `else` branches
Rules are also sorted alphabetically and I cleaned up various parts of
`.golangci.yml`.
|
| |
|
|
|
| |
Fix #29879
Co-authored-by: Giteabot <teabot@gitea.io>
|
| | |
|
| | |
|
| |
|
|
|
|
|
|
|
|
|
| |
Fix #29837 which is a regression caused by
https://github.com/go-gitea/gitea/pull/29145/files#diff-731445ee00f0f1bf2ff731f4f96ddcf51cdc53fd2faaf406eb3536fc292ea748L48.
The line was probably removed by accident.
---------
Co-authored-by: Giteabot <teabot@gitea.io>
|
| |
|
| |
Follow #29690
|
| |
|
| |
Fix #29689
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
Refactor the webhook logic, to have the type-dependent processing happen
only in one place.
---
## Current webhook flow
1. An event happens
2. It is pre-processed (depending on the webhook type) and its body is
added to a task queue
3. When the task is processed, some more logic (depending on the webhook
type as well) is applied to make an HTTP request
This means that webhook-type dependant logic is needed in step 2 and 3.
This is cumbersome and brittle to maintain.
Updated webhook flow with this PR:
1. An event happens
2. It is stored as-is and added to a task queue
3. When the task is processed, the event is processed (depending on the
webhook type) to make an HTTP request
So the only webhook-type dependent logic happens in one place (step 3)
which should be much more robust.
## Consequences of the refactor
- the raw event must be stored in the hooktask (until now, the
pre-processed body was stored)
- to ensure that previous hooktasks are correctly sent, a
`payload_version` is added (version 1: the body has already been
pre-process / version 2: the body is the raw event)
So future webhook additions will only have to deal with creating an
http.Request based on the raw event (no need to adjust the code in
multiple places, like currently).
Moreover since this processing happens when fetching from the task
queue, it ensures that the queuing of new events (upon a `git push` for
instance) does not get slowed down by a slow webhook.
As a concrete example, the PR #19307 for custom webhooks, should be
substantially smaller:
- no need to change `services/webhook/deliver.go`
- minimal change in `services/webhook/webhook.go` (add the new webhook
to the map)
- no need to change all the individual webhook files (since with this
refactor the `*webhook_model.Webhook` is provided as argument)
|
| |
|
|
|
|
| |
and migrate affected code
_last refactoring bits to replace **util.OptionalBool** with
**optional.Option[bool]**_
|
| |
|
|
|
|
|
|
| |
Go 1.21 improved the performance of `crypto/sha256`. It's now similar to
`minio/sha256-simd`, so we should just use the standard libs.
https://go.dev/doc/go1.21#crypto/sha256
https://go-review.googlesource.com/c/go/+/408795
https://github.com/multiformats/go-multihash/pull/173
|
| |
|
|
|
|
| |
Refactor Hash interfaces and centralize hash function. This will allow
easier introduction of different hash function later on.
This forms the "no-op" part of the SHA256 enablement patch.
|
| |
|
|
| |
For those simple objects, it's unnecessary to write the find and count
methods again and again.
|
| |
|
|
|
|
|
|
|
|
| |
Fixes #28088
Fixes #28094
Added missing tests.
---------
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
|
| |
|
|
|
|
|
| |
Fix #23742
---------
Co-authored-by: KN4CK3R <admin@oldschoolhack.me>
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
When `webhook.PROXY_URL` has been set, the old code will check if the
proxy host is in `ALLOWED_HOST_LIST` or reject requests through the
proxy. It requires users to add the proxy host to `ALLOWED_HOST_LIST`.
However, it actually allows all requests to any port on the host, when
the proxy host is probably an internal address.
But things may be even worse. `ALLOWED_HOST_LIST` doesn't really work
when requests are sent to the allowed proxy, and the proxy could forward
them to any hosts.
This PR fixes it by:
- If the proxy has been set, always allow connectioins to the host and
port.
- Check `ALLOWED_HOST_LIST` before forwarding.
|
| |
|
| |
Last part of #27065
|
| |
|
|
|
|
|
|
|
| |
This PR removed `unittest.MainTest` the second parameter
`TestOptions.GiteaRoot`. Now it detects the root directory by current
working directory.
---------
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| | |
|
| |
|
| |
Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
|
| |
|
| |
Extract from #22266
|
